
The multinational G oogle released another emergency update for Chrome, after having detected a new vulnerability in the system. It is the second fault, with its respective solution, that is released in just over a week.
On March 25, Google released an update after identifying a problem in the version of Chrome that could be being used by hackers, the company warned at the time.
The company explained on their blog that the update for Windows, Mac and Linux was already available under the numbering 99.0.4844.84.
The threat was considered “high” (the second most serious category only behind criticism), “until most users update” to prevent the dissemination of sensitive information without giving the average user the opportunity to be protected.
This vulnerability received the nomenclature CVE-2022-1096 and it was reported by an anonymous user on March 23. The company confirmed that an exploit of this flaw had been seen, which means that the attacks were already taking place.
Now a new emergency update has arrived. Although in this case, the point in favor is that, for now, there is no confirmation that the attackers are already exploiting the identified cybersecurity hole.
The emergency update arrives with version 100.0.4896.75. In an announcement released on April 4, Google confirms that the security patch will be rolled out to Chrome's Windows, Mac and Linux users in the coming days and weeks.
The vulnerability is listed as CVE-2022-1232 and is of high severity. The company has not yet given technical details about this flaw. As usual, it will do so when most Chrome users have been able to update the system. This is a precautionary measure that is usually implemented in these contexts.
According to the Center for Internet Security, this security hole could allow arbitrary code to be executed. This refers to an attacker's ability to execute commands or inject malicious code into an application.
“Depending on the privileges associated with the application, an attacker could view, change or delete data,” they warn from that entity.
Because the Chromium engine works with many browsers, including Edge and Opera, security updates will surely be released for them in the coming days as well.
How to update Chrome
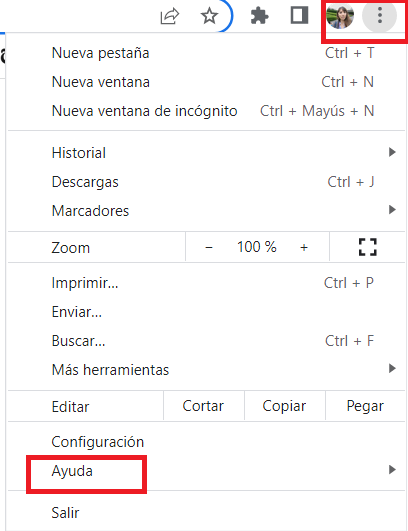
Tap the three dots at the top of Chrome, just below the profile picture. This will enter the Settings menu.
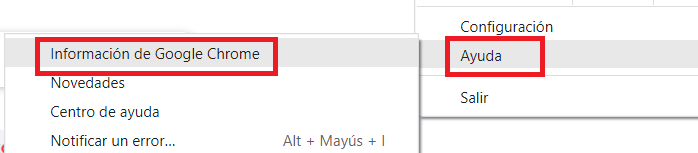
Then click on the option that says Help and then on Chrome information and there you will see the version you have. As mentioned earlier, the security patch for this flaw arrives with version 100.0.4896.75
If the aforementioned update is available, it will start downloading and otherwise we will have to wait a few days or even weeks as the company alerts on its blog. As this is a global launch, there may be delays.
Keep in mind that once the update is installed, it is necessary to restart the browser for the protection to be activated. Otherwise, the system will continue to be vulnerable to possible attacks that exploit the aforementioned flaw.
Other security measures:
Here are some security measures that must be implemented until the patch arrives and even after you receive it to add an extra layer of care, as mentioned on the Internet Security Center site
1. Run all software as a non-privileged user (one without administrative privileges) to lessen the effects of a potential attack.
2. Avoid visiting untrusted websites or clicking on links provided by unknown sources.
3. Inform and educate users about threats posed by hypertext links contained in emails or attachments, especially from untrusted sources.
KEEP READING:
Últimas Noticias
Debanhi Escobar: they secured the motel where she was found lifeless in a cistern

The oldest person in the world died at the age of 119

Macabre find in CDMX: they left a body bagged and tied in a taxi
The eagles of America will face Manchester City in a duel of legends. Here are the details

Why is it good to bring dogs out to know the world when they are puppies




